Azure SSO Integration
This topic is for Clients who log in using an Administrator Role. It assumes that you have nOps configured on your Microsoft Entra ID (This was formerly known as Azure AD).
Steps to configure Azure SSO integration with nOps
We suggest that you keep both the AWS and nOps platform open in the same browser to switch between during the steps.
-
Create an Enterprise Application inside Microsoft Entra ID
- Within your Azure portal, Navigate to Enterprise Applications → All Applications → New Application
- Fill in the name of your app (For example, “nOps SSO”)
- Keep the default option Integrate any other application you don't find in the gallery (Non-gallery).
- Click Create

-
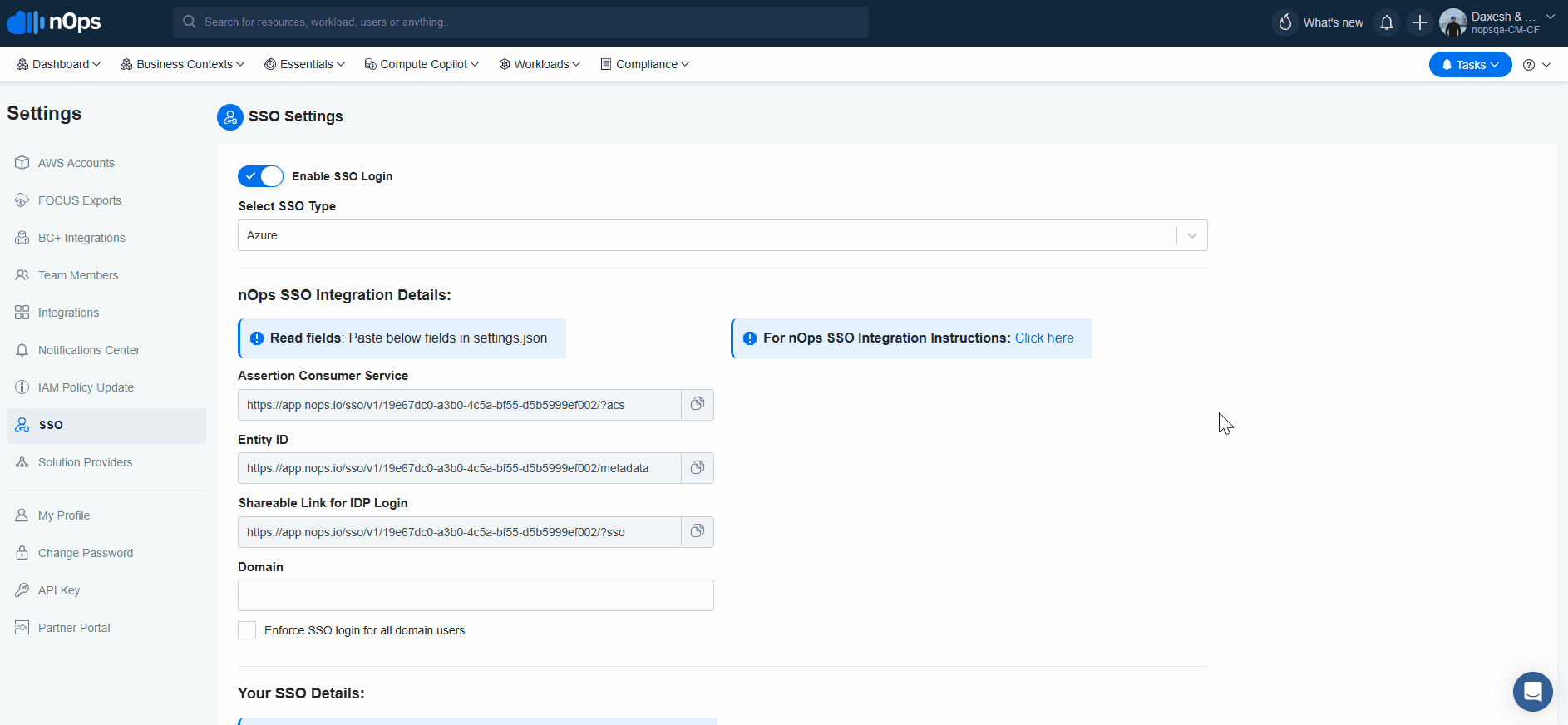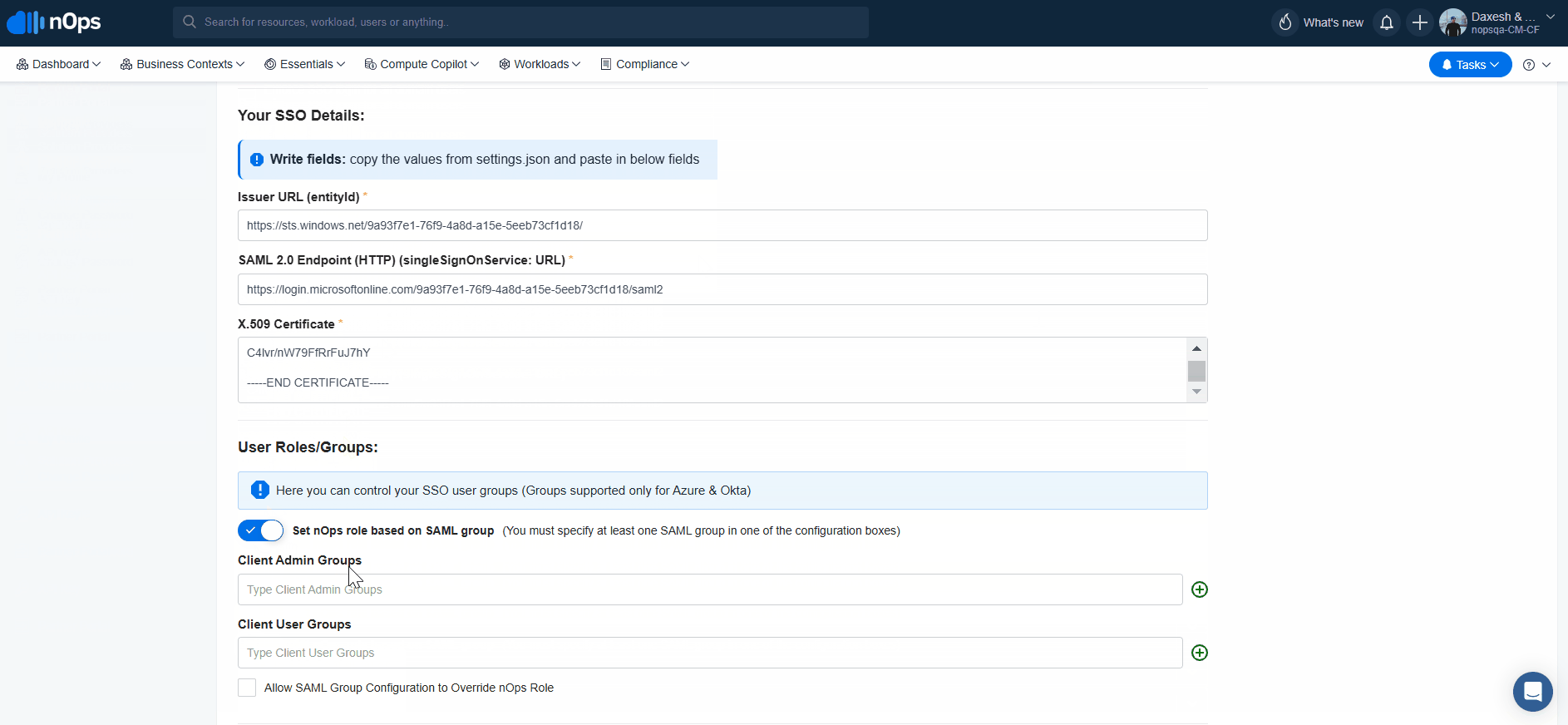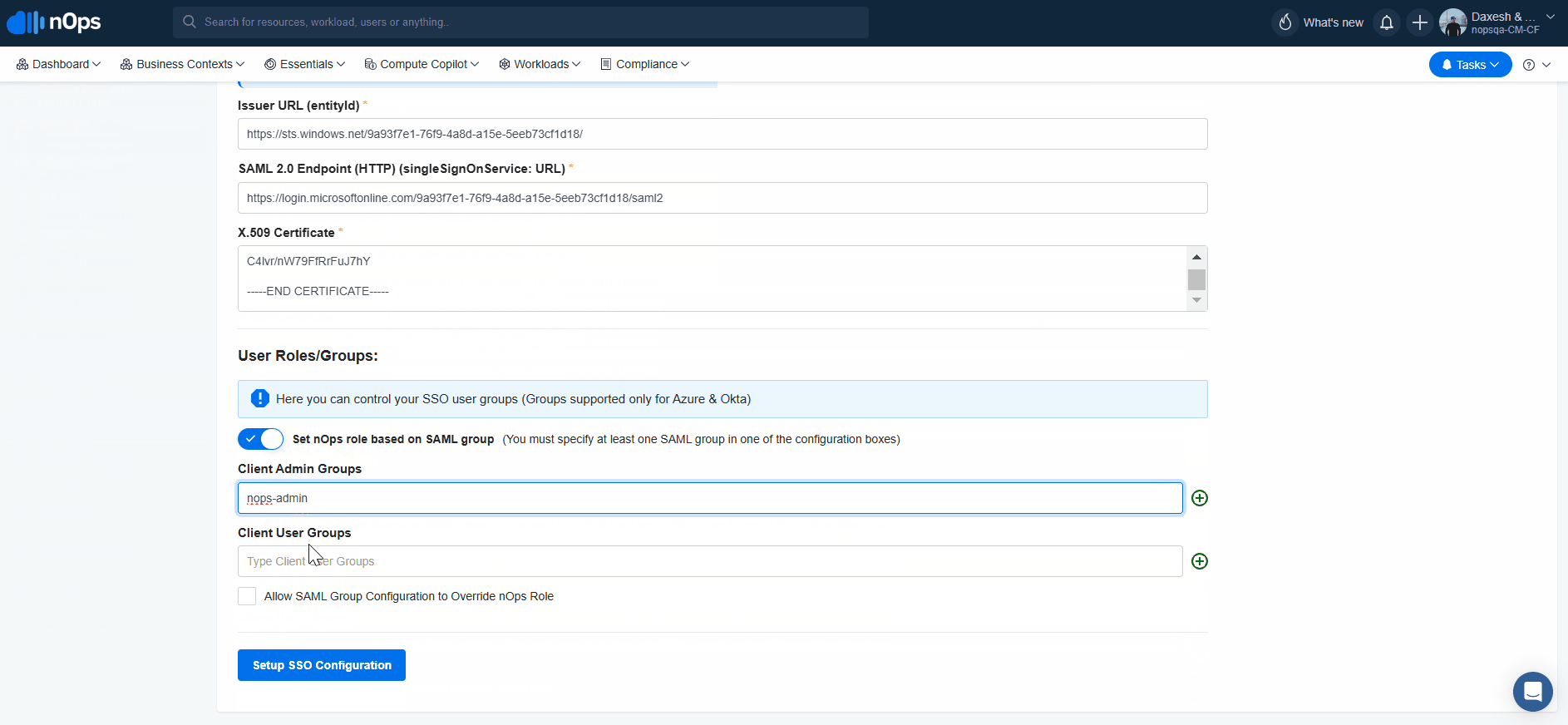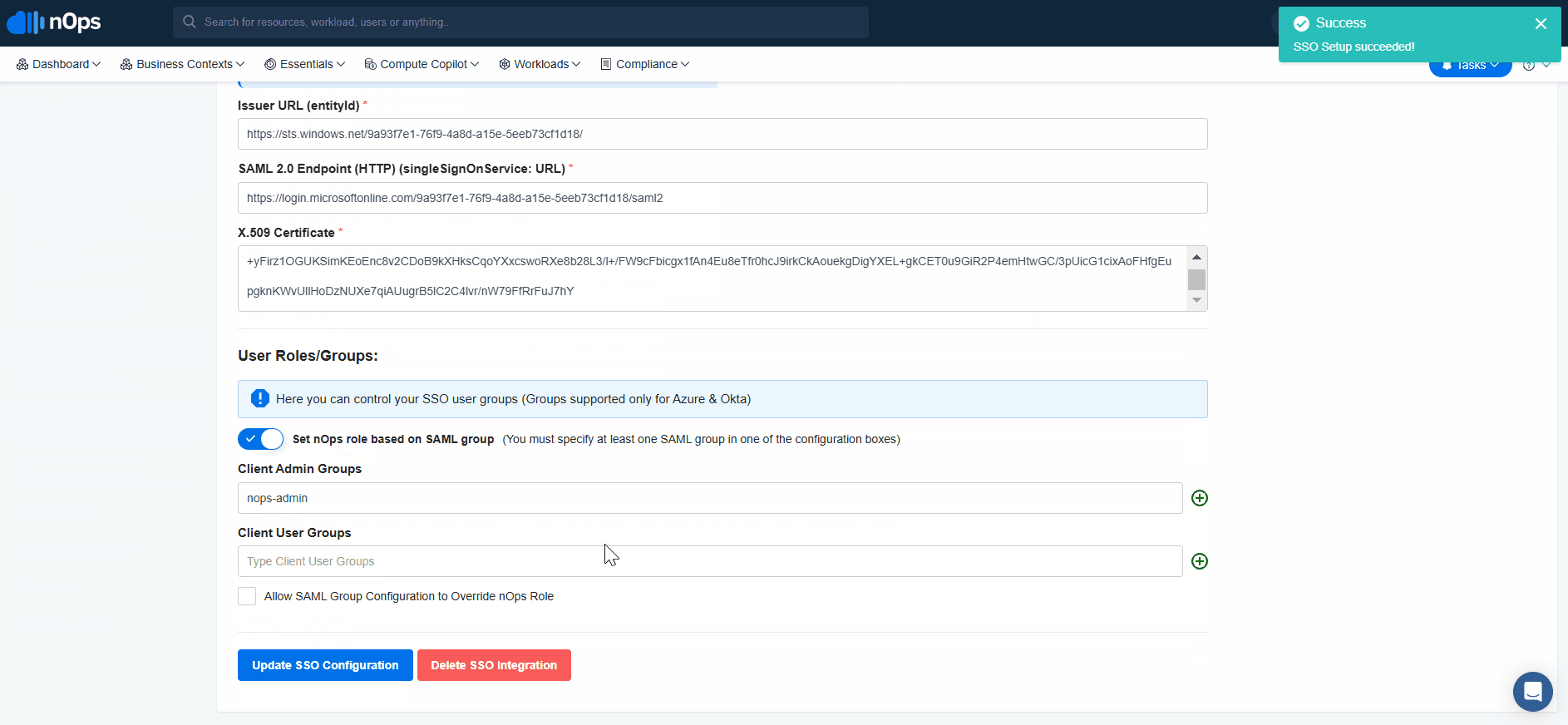
On the nOps platform, navigate to Organizational Settings → SSO to Enable SSO and Select SSO Type: Azure

-
Perform the following steps on the Azure Portal where Enterprise Application creation is in progress.
- In the getting started section, click Setup Single sign on
- Select SAML
- Edit Basic SAML Configuration
- Copy the Entity ID from nOps SSO integration Details and paste it into the Azure Portal → Enterprise Application → Basic SAML Configuration field Identifier Entity ID.
- Copy the Assertion Consumer Service URL from nOps SSO Integration Details and paste it into Azure Portal → Enterprise Application → Basic SAML Configuration → Reply URL (Assertion Consumer Service URL)
- Copy the Shareable Link for IDP Login from nOps SSO integration Details and paste it into Azure Portal → Enterprise Application → Basic SAML Configuration → Sign On Url.
- Save the details

-
Copy the Login URL from Set up nOps SSO and paste it into the nOps platform → SAML 2.0 Endpoint (HTTP) (singleSignOnService: URL)
-
Copy the Microsoft Entra Identifier from Set up nOps SSO and paste it into the nOps platform → Issuer URL (entityId)

- Download the IAM Identity Certificate.
-
Switch to the Azure Portal and download the Certificate (Base64) provided in the SAML Certificates section.
-
Open the downloaded Certificate into a text editor such as Notepad.
-
Copy the Certificate data and paste it into the nOps platform → Organization Settings → SSO → Your SSO Details section field: X.509 Certificate

- Navigate to Attributes & Claims: Configure Attribute mappings
-
Click on the Add new Claim button. You will need to add 3 new claims in the Manage claim screen with providing Name, Source & Source Attribute.
Name Source Source Attribute User.FirstName Attribute user.givenname User.LastName Attribute user.surname User.Email Attribute user.mail User.Groups Attribute user.groups
- Group Claims: Configure Group Claim Mappings
Steps to Configure Group Claims
-
Navigate to the Azure Portal:
- Go to Attributes & Claims in your application.
-
Add a Group Claim:
- Click on Add a group claim in the Manage claim screen.
Option 1: For Organizations with Active Directory Plan Support for Groups (Recommended)
-
Selection:
- Choose Groups assigned to the application.
-
Source Attribute:
- Set Source Attribute to Cloud-only group display names.
- This provides the friendly names of groups assigned to SSO.
Group names can be duplicated if they are not unique within your directory. Plan accordingly.
Option 2: Using Group IDs if you don't have plan support
-
Selection:
- Choose All groups.
-
Source Attribute:
- Select Group ID.
-
Customize the Group Claim:
- Expand Advanced Options and fill in the fields as follows:
- Name (required):
User.Groups - Namespace (Optional): Leave this field blank.
- Name (required):
- Expand Advanced Options and fill in the fields as follows:
If editing existing attributes, ensure the namespace field is cleared to avoid conflicts.
- Save the Configuration:
- Once configured, save the group claim settings.
The namespace field must be blank, if you are editing existing attributes make sure to delete the namespace.
7. Set nOps role based on SAML group and provide Group Names.
-
Navigate to Organization Settings → SSO and select Set nOps role based on SAML group for your User/Groups.
-
Provide admin or user groups you want to assign.
 note
noteIf you used the Group ID you must copy the Object ID value for the groups you used
-
Click on Setup SSO Configuration
-
Switch to Users and Groups to Create Groups and Users, and assign them in the nOps SSO Application.
-
Go to Test single sign-on with nOps SSO and click Test sign in.
-
A confirmation email should appear on your Microsoft email portal. Click to confirm and allow access.
Email Copy
Retry Test single sign-on with nOps SSO and click Test sign in. You should now be able to log into your nOps account.